Ransomware – The newest threat
Do you have any idea about Ransomware?
Ransomware is a kind of malware which prevents you from accessing your system or files. It forces you to pay a ransom via online to get a decrypt key. A ransomware are called a cryptovirus, cryptotrojan or cryptoworm.
Ransomware Infection
- Can be Downloaded to the systems when users visit malicious or compromised websites.
- Can be arrived as a payload of another malware.
- Delivered as an attachment from spammed email.
- Downloaded through malvertisements.
- Dropped by exploit kits.
How it works?
It encrypts its victims’ files, and then refuse to provide the key to unlock the files unless a payment is made within the given time period.
Some attacks put time pressure on victim. It says to pay within a certain time period to decrypt your data.
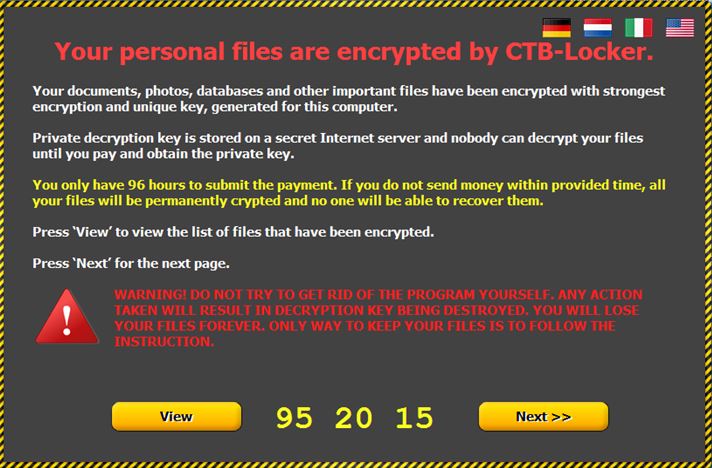
They may ask for a nominal payment.
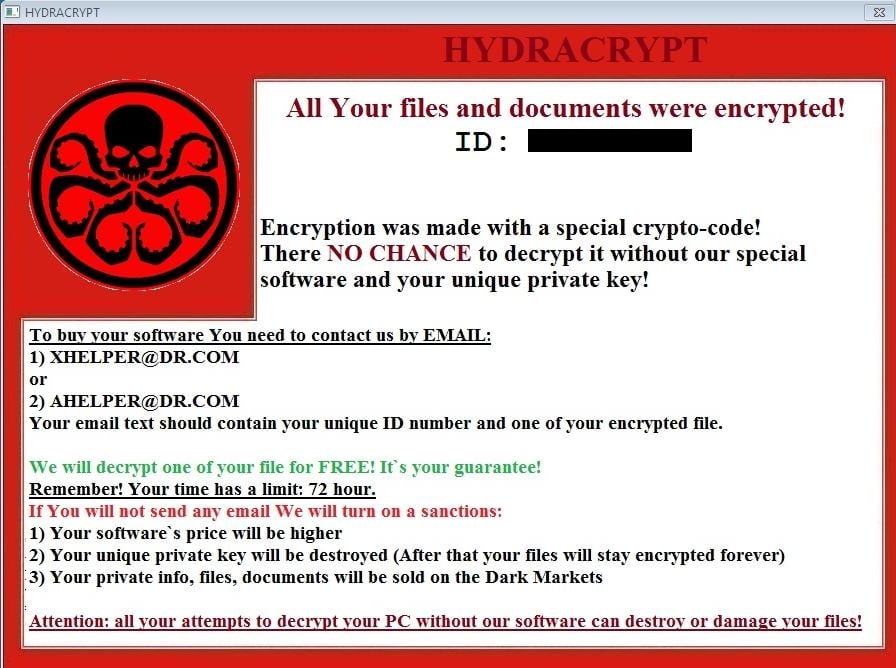
Ransomware attacks are entering to a system,such as a downloaded file or a vulnerability in a network service. The program then runs a payload, or claims to lock the system but does not. Payloads may display a fake warning .Some payloads consist of an application which locks or restricts the files until the payment is done. The most sophisticated payloads encrypt files.
Payment is virtually always the goal, victim is supposed to make the payment to decrypt the files, which may or may not actually occur.
Types of Ransomware
- Cryptolocker- It targets computers running MS Windows. This propagate via email attachments. When it activated, the malware encrypts files. The private key stored on the malware’s control servers. Then it displays a message which offers to decrypt the data after the payment is done before the deadline.If the payment is not done by the victim then the payment is higher than before.
- CryptoWall- It infects your computer and takes your data hostage.
- Locky- It is delivered by email with an attached MS Word document that contains malicious macros. When the user opens the document,among some unnecessary things a phrase will appear with a message to enable macro if the data encoding is not in a correct way.As soon as the user enables macros, the macros then save and run a binary file which downloads the encryption trojan, it will encrypt all the files with particular extensions. Filenames are converted to ‘.locky’ file extension. After encryption it will direct the user to the hackers site for further information.Then they demands for a payment.
- TeslaCrypt- This is no longer functioning.Its master key was released by the developers. You can find free decryption tool in the web.
- TorrentLocker-This targets all versions of windows.
- KeRanger- This targets computers running OS X.
Prevention
- Always run a good antivirus utility.
- Keep Windows and browser-related components updated.
- Keep your browser clean to prevent adware invasions that could lead to malware infections
- Be aware of unexpected email attachments and spams.
- Try to have a good backup system.
- Enable your popup blocker.
How to remove ransomware
- If your web browser is blocked : Close the web browser from the task manager. Open up the browser again the it will ask you whether you want to restore the sessions. Don’t restore them again.
- If your PC is locked : download a copy of the Microsoft Safety Scanner from a non-infected PC. Copy it to a portable data storage. Put it into the infected PC and restart it.Then run it on the infected PC when it is in safe mode.
- If you are locked out of your PC: ransomware can lock you out of your PC.Then you are not in a position to download or run the Microsoft Safety Scanner.So then you need to use the free tool “Windows Defender Offline”.


Helpful information… Thanks!
Thanks Sadun Mendis. keep on reading.
Good Work. Simple language, anyone can understand it.
Thanks Wishwa Hettige. Keep in touch.